Two years after WannaCry, a million computers remain at risk
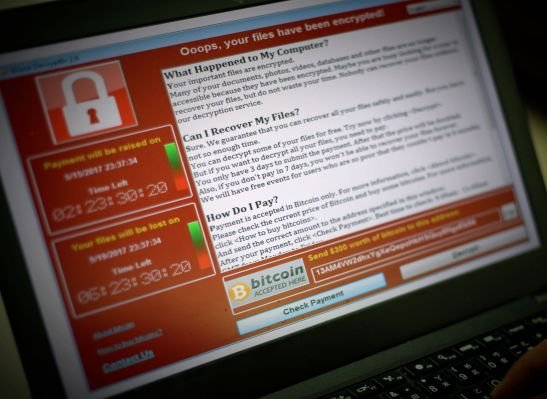
Two years agotoday, a powerful ransomware began spreading across the world.
WannaCry spread like wildfire, encrypting hundreds of thousands of computers in more than 150 countries in a matter of hours. It was the first time that ransomware, a malware that encrypts a user’s files and demands cryptocurrency in ransom to unlock them, had spread across the world in what looked like a coordinated cyberattack.
Hospitals across the U.K. declared a “major incident” after they were knocked offline by the malware. Government systems, railway networks and private companies were also hit.
Security researchers quickly realized the malware was spreading like a computer worm, across computers and over the network, using the Windows SMB protocol. Suspicion soon fell on a batch of highly classified hacking tools developed by the National Security Agency, which weeks earlier had been stolen and published online for anyone to use.
“It’s real,” said Kevin Beaumont, a U.K.-based security researcher at the time. “The shit is going to hit the fan big style.”
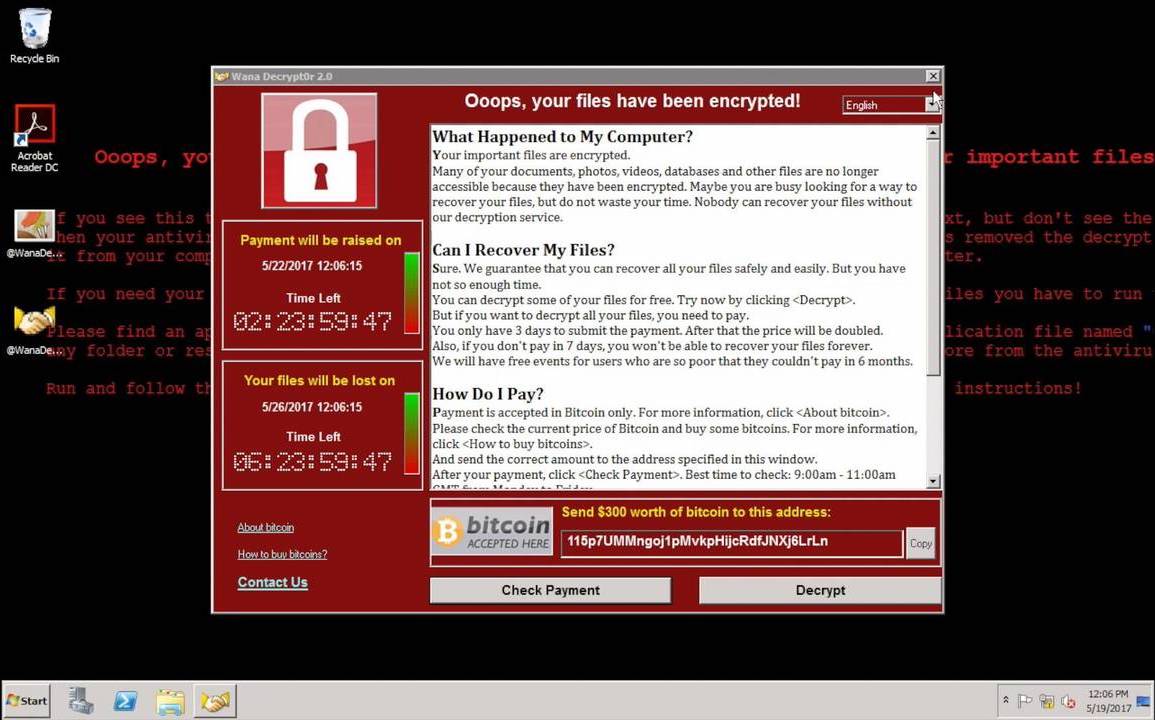
WannaCry relied on stolen NSA-developed exploits, DoublePulsar and EternalBlue, to hack into Windows PCs and spread through the network (Image: file photo)
An unknown hacker group — later believed to be working for North Korea — had taken those published NSA cyberweapons and launched their attack — likely not realizing how far the spread would go.The hackers used the NSA’s backdoor, DoublePulsar, to create a persistent backdoor that was used to deliver the WannaCry ransomware. Using the EternalBlue exploit, the ransomware spread to every other unpatched computer on the network.
A single vulnerable and internet-exposed system was enough to wreak havoc.
Microsoft,already aware of the theft of hacking tools targeting its operating systems, had released patches. But consumers and companies alike moved slowly to patch their systems.
In just a few hours, the ransomware had caused billions of dollars in damages. Bitcoin wallets associated with the ransomware were filling up by victims to get their files back — more often th
Be the first to write a comment.








