Everything you need to know about ransomware in 2019

Fabian Wosar makes a living ruining ransomware gangs’ days, and he has the hate-mail to prove it.
“At one point, I managed to annoy a ransomware author so much that they literally renamed their ransomware in my name,” he says. “So they renamed their ransomware to ‘fabiansomware’, which is kind of really bizarre.”
Wosar is the head of research at IT security company Emsisoft, whose free ransomware decryption tools have been downloaded over a million times (1,144,351, to be exact, not including downloads from mirror sites). With the average ransomware writer demanding $522 (about £400, AU$750) to restore victims’ files, that’s a potential $597,351,222 (about £455,000,000, AU$833,000,000) kept out of the pockets of ransomware authors. Not bad for a 40-person company without an office.
“Emsisoft started out as a very, very small company with only two employees,” says Wosar. “When you try to get into the antivirus and antimalware field and you only have two people, there’s no way you can compete based on manpower with the big houses like Symantec and Kaspersky or Bitdefender, which all have thousands of employees.
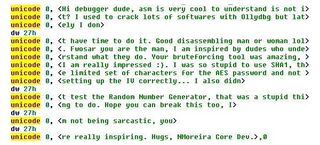
Not all the comments Wosar receives are insults; some ransomware authors are impressed
“It was very evident from the very beginning that we just have to be more agile, that we need to make sure that all our internal processes have a lot less overhead and we also had to be a lot smarter about how we put our limited resources to good use. And this business mindset that was originally born as kind of a necessity soon became the core philosophy behind all our products.
Emsisoft has grown steadily over the last 15 years, with no outside investment. It’s still a lot smaller than many of its rivals, but that hasn’t stopped it competing with the security software giants.
“We started out very much as a very home user focused company,” Wosar says, “but we started moving into the business market in recent years, with growing success and we came to realise that home users and enterprises often have vastly different requirements and needs. Most traditional companies solve that by just throwing more resources at it, and often splitting the product line, having different products for different clienteles, but that’s something that we simply can’t do.
“So our philosophy of keeping things lean we now focus on making all these advanced enterprise-level protection features not only available to home users, but also to make them approachable and useful to them so they can actually understand them and know what is happening, and putting the user into power by making them a lot more accessible, which will become a lot more eminent with a couple of upcoming products that we are going to release in 2019 that I can’t tell much about. But that’s out focus now, just giving the power to the man.”
A brief history of ransomware
Wosar’s interest in security began when he was just 11. “I got infected by a virus called Tequila in the good old DOS days, and I just got kind of drawn in,” he says.
He first became interested in ransomware in 2012, when BleepingComputer founder Lawrence Abrams asked if he could help some forum users who’d fallen victim to the ACCDFISA (Anti Cyber Crime Department of Federal Internet Security Agency) virus – one of the first examples of file-encrypting ransomware.
“Ransomware first became big in the form of screen lockers,” Wosar explains. “Essentially you’re browsing the internet and suddenly a screen pops up locking your entire screen, telling you the FBI or GCHQ just saw you doing something naughty. Now you have to go to your local store and pick up a Paysafecard and type in the code to unlock your system. Because obviously the state would take Paysafecard, right?”
That is always kind of interesting, when people get so angry that they want to insult me so badly that they actually end up making their ransomware less secure in the process
Fabian Wosar, Emsisoft
It soon became common knowledge that screen lockers were relatively easy to remove (just restart the computer in Safe Mode and remove the infection), so the people behind them turned to file encryption instead. This is a much bigger issue, and one that Wosar has dedicated years to tackling – much to the annoyance of the criminals.
Wosar receives regular insults, and often finds them within the ransomware itself, which can have unintended consequences.
“There’s a certain kind of encryption called a block cipher that operates on blocks of data,” Wosar says. “When you think about it, if you don’t change your encryption from block to block, then even if you only have an encr
Be the first to write a comment.